“If you know the enemy and know yourself, you need not fear the result of a hundred battles.” – Sun Tzu, The Art of War
It seems that every other week, a major data breach has occurred. Exposing personal information of often thousands of customers. And that’s of the breaches that we are made aware of. According to a 2020 CyberVentures articles, the cost of cybercrime was estimated to be an annual $10.5 trillion by 2025. That is a lot of money. To put that into perspective. $10.5 trillion is equivalent 14 trillion 51g Mars bars. That is a lot of Mars bars. But how do cybercriminals do it? Has anyone asked them? That’s where the Cyber Kill Chain comes into play.
A kill chain is a military term describing a model of the strcture of an attack. The Cyber Kill Chain is a framework made by Lockleed Martin, which describes the various stages of a cyber attack by an adversary. There are seven stages.
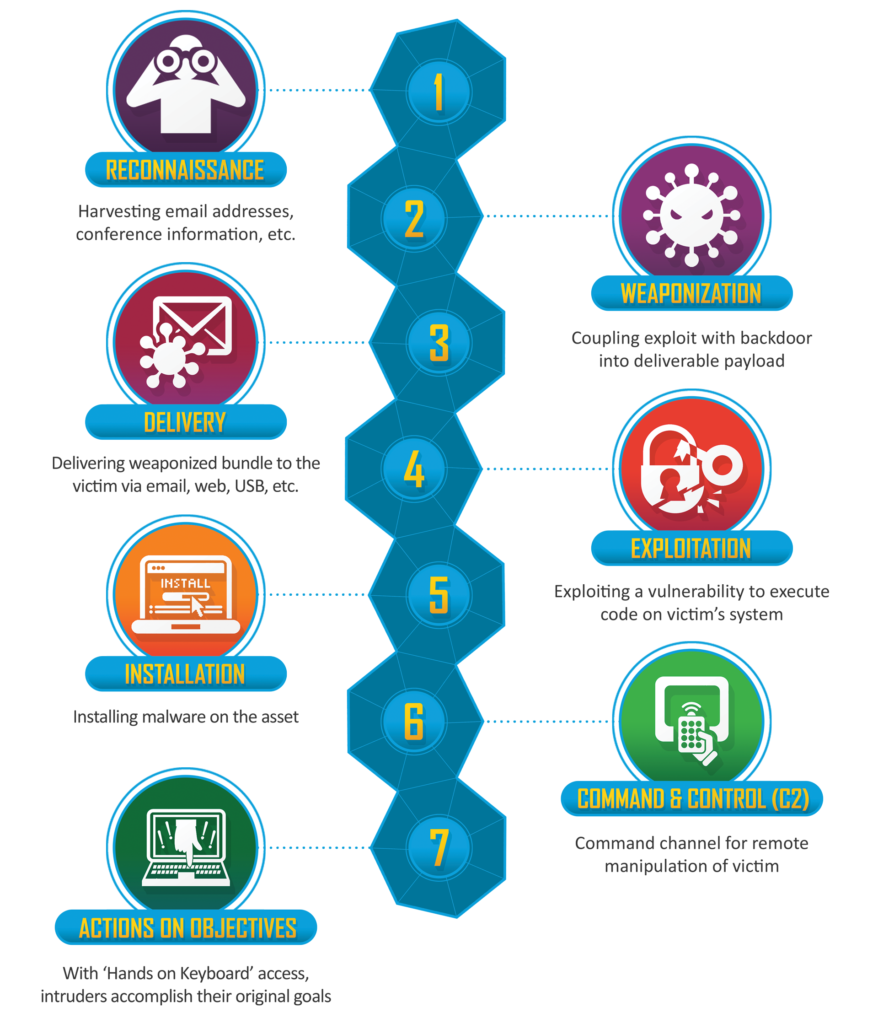
Stage 1 – Reconnaissance: Before you pull off a daring heist, you have to scout it out. Get the lay of the land. What walls are deteriorating? Where do the guards patrol? How often do they patrol? Such information is critical if you want any hope of a successful heist. This is exactly the same in cyberspace though the questions are a little different. What information can be found in the public domain (OSINT)? Can we get an insider threat that can give us information about the network or, better still, perform certain actions for us? Attackers gather as much information as they can. This process can potentially take months depending on the target.
Stage 2 – Weaponization: Using the information collated in the previous stage, the attackers may find a device on the network that hasn’t been used or updated in years or poor account access control. This is the point where attackers develop (or buy) malware attacking vulnerabilities found. As the name of the stage suggests, this malware is what allows them to attack a network.
Stage 3 – Delivery: The attackers now have a bespoke weapon to attack their target, but it isn’t much good in their own network. They got to deliver it. Despite the sophistication and expertise behind the former stages, the execution of this stage can be rather crude. It could be a widespread email sent to all employees telling them that they have an outstanding invoice and to download the attached zip file. Most people would ignore it but maybe someone has been recently on-boarded and want to make sure that they are due diligent. They now have downloaded malware onto their company device. Oh dear. Why even waste the time writing an email? Just drop a USB in the company parking lot. Someone will pick it up and plug it into a company computer.
Stage 4 – Exploitation: There is now malware in the target device in the target network. During this stage, the code is executed and exploits a specific vulnerability on the target network.
Stage 5 – Installation: This is where the malware is installed, which gives it access to the operating system of the device it is on and so it computational resources. A backdoor is installed in the target network so that the attackers can have access to the network.
Stage 6 – Command & Control: Sometimes shortened to C2, this stage highlights the point where the attacker has keyboard access also known as persistent access to the target network. They use the infected device as a launchpad to carry out further attacks or move laterally in the network. They may attempt to escalate their priviledges to perform even more devastating attacks. They may introduce even more points of entry for the future in case the security team patches up the original point of entry.
Stage 7 – Action on Objectives: The attackers now have full control over a portion of the network. They now can carry out their objectives: what they actually want to do against the target. There are many different motivations for hackers to hack. They could be hactivists who have political motivations and may wish to disrupt a company’s functions. They may be state actors who hack on behalf of their government to attack an opposing government’s IT infrastructure. They may be your run-of-the-mill cybercriminal who just want to extort money from the company. Ransomware is a prime example of this kind of extortion, where data is encrypted and adversaries demand payment in exchange for decryption of those files that may potentially contain critically sensitive information.
I hope this has helped you to understand what the Cyber Kill Chain is and how it can be used to model attacks conducted by adversaries.
Until next time.
Leave a Reply