Computers are complicated. Networks of computers are even more complicated. Computers and applications communicate with one another using various protocols and software. That last sentence is very vague and really doesn’t give any real insight on how computers communicate with each other, whatever that means. Is there a way to break down and categorise this communication? Yes and it’s called the Open Systems Interconnection Model, shortened to OSI Model.
It has several layers starting from layers that are interacted with by the end-user all the way to the physical layer. The OSI Model is a conceptual framework which generally describes computer networking. This allows for one to readily troubleshoot any networking issues by going through each layer.
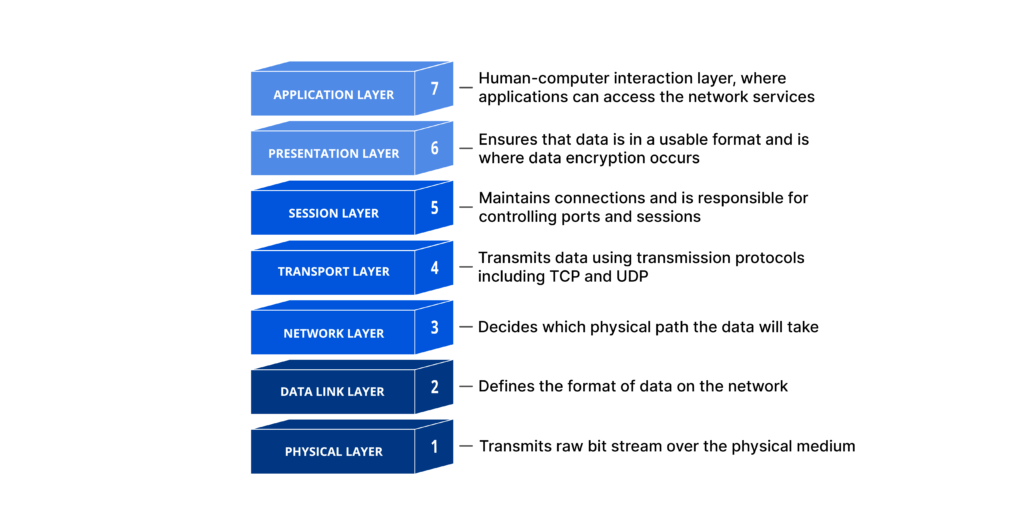
Ref: https://www.cloudflare.com/en-gb/learning/ddos/glossary/open-systems-interconnection-model-osi/
So let’s start from the ground up with the first layer and one of the easiest ones to understand: the Physical layer. This layer represents the actual hardware that is involved in the network. If the server or database that you are connecting to isn’t actually turned on and has power, then how can you expect to remotely access it from your personal computer/client. In that sorry excuse of cable management, are one of the cables not plugged in? You have to make sure that the physical equipment are actually functioning. The bottom-most layer also refers to the raw bits (quite literally 0s and 1s) of any data that is to be sent.
Layer 2 is the Data Link layer, organises the aforementioned raw bits into frames, which are the network units of Layer 2. It moves data into and out of physical data links (Layer 1). The ethernet protocol resides in this layer and establishes local area networks (LANs) of multiple computers. The second layer consists of two parts: Media Access Control (MAC) and Logical Link Control (LLC). MAC is the lower-level layer of the two and is responsible for communicating with the physical layer. LLC uses the services provided by MAC to establish connections with other machines in the LAN. This layer makes sure that the generated frames are sent to the correct place without error.
Layer 3 is quite similar to the previous layer as it covers Networking. If the previous layer covered data transfer in the same network, this one covers data transfer between different networks. Instead of using frames as a standard unit, this layer uses the more familiar packets. The sending device breaks up these packets and sends them to the receiving device where it is reassembled. The Internet Protocol (IP) which routes data from one network to another is found here.
Layer 4 is the all-important Transport layer where the data is actually transported. The two main protocols involved in this layer are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). TCP requires a connection between two computers, is slower but corrects any errors that may arise during transport. Thus this protocol is often used for web browsing, emails, and downloading files. UDP does not require a connection, is faster but does not correct errors. This protocol is used for video streaming and online gaming. Layer 4 splits the data into smaller segments before sending it across the web. The layer also manages flow control which means that the rate of data transfer is the same as the connection speed of the receiving device.
Layers 5 and 6 are sometimes considered too specific and not fit for practical purposes and there is a conceptual model called the TCP/IP Model which is the same as the OSI Model but combines Layers 5, 6, and 7 into an “Application Protocols” layer (often still called Layer 7 confusingly). However, for completion I will briefly cover these layers. Layer 5 is the Session Layer is responsible for opening and closing communications between devices in channels called sessions. The layer also establishes checkpoints for data to be re-sent from in the event of an error. Layer 6 is the Presentation Layer and makes sure that any data is translated such that the final layer can interpret it. This could be making sure data is decrypted at the receiving or maybe the devices use different embedding methods.
Layer 7 is the Application Layer. This layer covers the protocols that are used behind the scenes in the various applications used by the end-user that make data human-readable. Note that this layer covers does not the applications (eg. email client, web browser) themselves.
I hope this has helped in your understanding of what the OSI Model is and a general sense of how networking works.
Until next time.
Leave a Reply