There have been many legendary pyramids throughout human history. Chichen Itza. The Great Pyramids of Giza. The Food Pyramid. Each of which is a feat of human engineering. But none are as disappointingly mediocre as the Pyramid of Pain.
The Pyramid of Pain is a cybersecurity framework that is mainly used in incident response. Incidents are events that breach an organisation’s security policies and so incident response is how an organisation deals with any such breaches though the phrase is normally exclusively used in conjunction with data breaches.
The Pyramid of Pain is used to model an adversaries assets such as any malware used in a cyber attack or characteristic techniques used by known cybercriminal groups. As the name implies, there is a hierarchy of how troublesome it is for an adversary to change their approach to an attack if defensive measures are implemented against certain adversial assets. Let’s go through each of the layers in turn starting from the bottom.
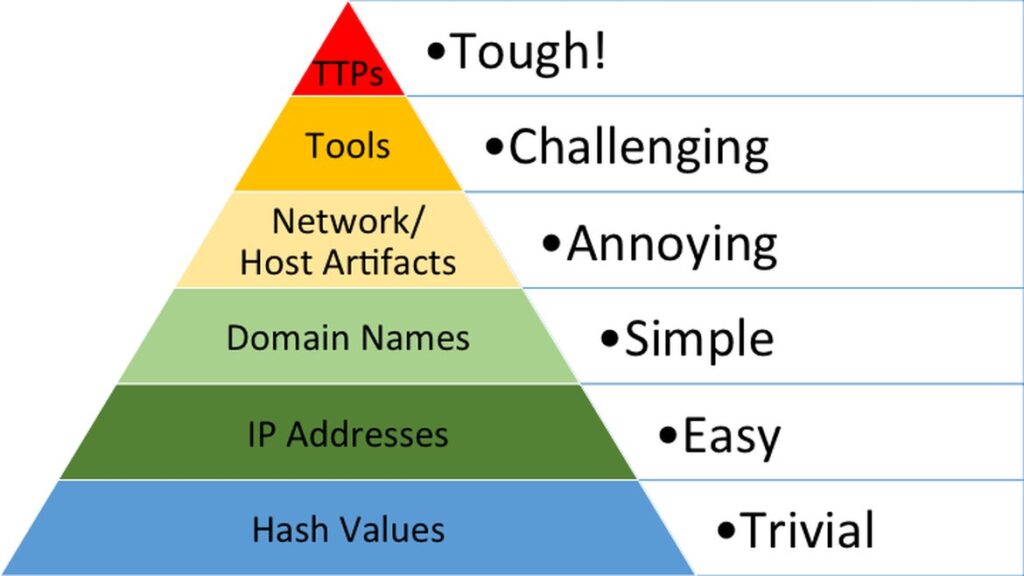
Hash Values refers to simply the hash values of any malware files that are found and linked to the attack. Hash values are fixed-length strings that are unique to a file’s contents. Hash functions are used to generate these values and are very difficult to inverse. They can be thought as a file’s fingerprints. However, it doesn’t much alteration to completely change the hash value of a file as shown below.
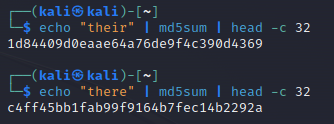
So if a specific hash value is filtered out by a network’s firewall, all the adversary would need to do to circumvent that is add a character somewhere in the file.
IP Addresses are the basis of any connection over the Internet. If an adversary makes a connection to a victim network, they must have an IP address in order make that connection. Unfortunately it is very unlikely for an adversary to be using their home desktop in their bedroom, they would likely be using proxies, which are just computers that they remotely connect to so that those computers can make the connection for them. So to get around any firewall rules regarding IP addresses, all they would have to do is connect to a different computer. There already exists things like VPNs and Tor, which can continuously alter one’s IP address. So like the Hash Values layer, this type of defence isn’t very strong.
Domain Names are human-readable strings that are used to translate IP addresses so the Internet is easier to navigate (eg. google.com instead of 8.8.8.8). Domain names must be registered by a domain name registrar, which can cost money and take up time therefore they are harder to change than IP addresses. Some registrars though have lax standards and some provide APIs to allow their users to change their domain names more easily. Again it is not an insurmountable task for an adversary to change it.
Network/Host Artifacts. Now we have entered the territory were it is bothersome for the adversary and the defence is more effective. This layer refers to any artifacts that can be seen that differentiate legitimate and malicious activity. An adversary’s HTTP reconnaissance tool may have a distinct User-Agent string and so this activity can be blocked. The adversary would then need to spend time trying to figure out how they were detected and then try to fix it. These artifacts also extends to any files, directories, registry objects, and URL patterns.
Tools is the point where the defenders are picking up so many artifacts from a specific tool or successfully identified that the attacker is using that the attacker may give up using that tool. This means that they would need to find and train themselves on a new tool which can be used for the same purpose or if competent enough they may develop their own tool. Either way it is very time-consuming for the adversary to change their course.
TTPs standing for Tactics, Techniques, and Procedures refers to when the specific techniques used by the attacker are correctly identified. This is when the attacker would have to completely reinvent themselves to have any chance of continuing their attack on the victim network. Or they could just give up. And the latter is the precise option that most attackers would take.
I hope this has helped in your understanding of what the Pyramid of Pain framework is and how incident responders may categorise different attack indicators.
Until next time.
Leave a Reply