Whenever you send a message, there is always the concern of whether a malicious third party will intercept it and run with the precious information contained within the message. If we were talking about physical messages like handwritten letters, there isn’t much that can be done about it if the envelope is retreived by someone other than the intended recipient. You could hire guards for the trustworthy messenger so that no bandits may take the message by force and then sell any valuable information in the black market or even make use of the information themselves. But hiring guards isn’t cheap and numbers can defeat even the most well-trained of soldiers. If we can’t prevent the interception of the message, is there another way to prevent the bandits from reading the message (besides illiteracy)?
The answer is the title of this post. Encryption.
The earliest use of encryption was by Julius Caesar with the aptly named Caesar cipher. The encryption is quite simple for the modern day. A substitution algorithm where each letter in the message is replaced by the letter three places ahead of the original letter in the alphabet (eg. A -> D, Z -> C). This generates the unreadable gibberish known as the ciphertext. To then decrypt this ciphertext, you would use the inverse of the encryption process and so you would shift back the alphabet by three places instead of forwards (eg. D -> A, C -> Z). This generates the original readable message also known as the plaintext.
This ciphertext is nonsensical to any intercepters but can be converted to plaintext by the intended recipients who know how to decrypt it. This means that even if the message is intercepted, there is no way of learning anything meaningful about the message. Only the sender and the intended recipient have access to the key, which is used to decrypt it. When the secret keys, established by the sender and the recipient, are the same, this is known as symmetric encryption.
Now let’s move on to the modern world. The internet is a very popular place. We use it in all sorts of applications, we use it for entertainment, making connections with other users, and for research purposes. In the end, all these things are possible because of a vast number of “messages” (more specifically data packets) that are sent between two computers that are connected to the internet. When you open a web page like this one, your computer is actually establishing a connection to a web server, which serves your browser, the client, the website.
And like our metaphorical scenario at the start, these messages can be intercepted though the methods are more complicated. This becomes an even more significant issue when these messages are used for logging into your bank account or financial transactions. Instead of sending these messages in plaintext, we can make sure that they are encrypted in transit. There are two types of encryption: the aforementioned symmetric encryption and asymmetric encryption. Each kind of encryption has a plethora of different algorithms. These algorithms evolve, and new ones are introduced as security vulnerabilities are discovered and computers become more powerful.
Regarding the former, symmetric encryption involves a shared secret between two parties. They are used for encrypting large blocks of data as it is faster than its asymmetric counterpart but at the cost of being less secure. Asymmetric encryption involves two keys: a private key and a public key.
As the name suggests, the public key can be given to anyone freely. If Person A wants to send a message to Person B, Person A must ask Person B for their Public Key B. Person A uses Public Key B to encrypt their message and sends it to Person B. Person C intercepts the message and attempts to decrypt it using Public Key B, falsely assuming it to be a shared secret key between Person A and Person B, and cannot decrypt it. Person B, the intended recipient, receives the message and simply decrypts the message using Private Key B. This process ensures that the message only goes TO Person B as only they can decrypt and read it.
We have a way to prove that a message only goes to the intended recipient, but how do we prove that a message could only come FROM Person B. This is where digital signatures come into play. Person B wants to prove that their ground-breaking article about the 10 ways of passing the butter could only come from them. Person B now signs the article using Private Key B and broadcasts it. Person A and Person C read the article and think that there is no way this revolutionary text could be produced by Person B. They both use Public Key B and they each validate the digital signature on the article. They are surprised to learn that it was indeed written by Person B.
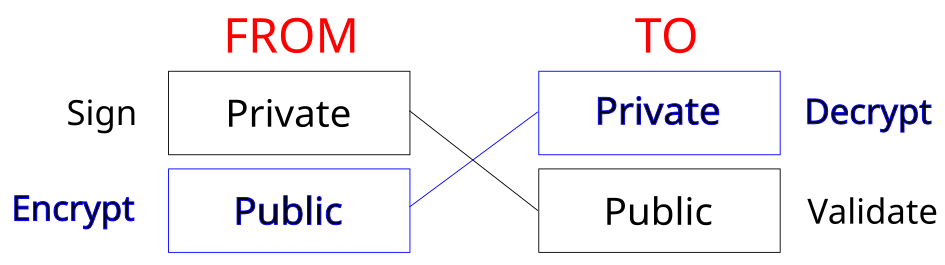
Asymmetric encryption is far more secure then symmetric encryption but with the increased number of steps, it is slower and requires more computational resources. It is used to encrypt small but very important bits of data such as financial transactions.
I hope this has helped your understanding of the differences between symmetric and asymmetric encryption and what they are used for.
Until next time.
Leave a Reply